
Security researchers just analyzed 6 billion leaked passwords. The results are embarrassing.
The top five most-stolen credentials haven’t changed in years. People still use “123456” and “password” despite endless warnings. Meanwhile, five malware families stole nearly 100 million login details in 2025 alone.
Here’s what the data reveals about password security—and how to actually protect yourself.
The Same Terrible Passwords Win Again
Specops Software examined 6 billion compromised passwords over the past year. The most frequently stolen credentials are painfully predictable:
Top 5 Most Stolen Passwords:
- 123456
- 123456789
- 12345678
- admin
- password
Notice the pattern? Most people don’t even bother choosing actual words. They just type numbers in sequence or use default credentials.
Beyond the top five, researchers found countless variations of “hello,” “welcome,” “guest,” and “student.” These aren’t just personal accounts. Companies, universities, and public systems use these weak passwords too.
The classic “qwerty” still appears frequently. So do passwords ending in “@123” or “@1234,” usually preceded by a name or country. Not exactly creative security.
Eight Characters Doesn’t Mean Eight Layers of Protection
Here’s an interesting finding. Most stolen passwords measure exactly eight characters long—about one-sixth of the total dataset.
Why eight? Probably because “password” has eight letters. Many systems also set eight characters as the minimum requirement. So people type the bare minimum and call it secure.
Adding a capital letter and special character doesn’t help much if everyone follows the same pattern. Hackers know that “Password!” and “Welcome@123” are common variations. These predictable patterns fall quickly to automated attacks.
Meanwhile, passwords shorter than seven characters are relatively rare. At least users understand that “123” won’t cut it anymore.
Five Malware Families Dominate Password Theft
Between January and December 2025, five infostealer programs accounted for nearly 100 million stolen login credentials:
LummaC2: 60.9 million stolen passwords
RedLine: 31.1 million stolen passwords
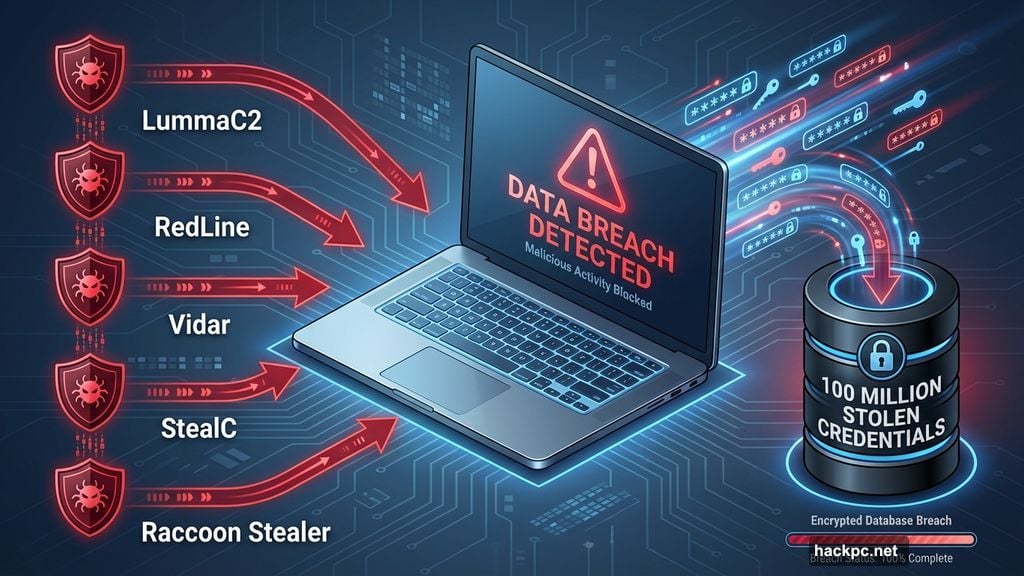
Vidar: 6 million stolen passwords
StealC: 3.4 million stolen passwords
Raccoon Stealer: 1.7 million stolen passwords
LummaC2 jumped to the top of the threat list this year. Its creators developed increasingly sophisticated packages that bundle multiple attack methods together.
These programs target less tech-savvy users through phishing campaigns. One click on a malicious link, and the malware installs itself. Then it quietly harvests every saved password on your device.
Password leaks happen at massive scale. A single breach can compromise millions of accounts simultaneously, as the FBI-powered leak in December demonstrated.
Real Protection Goes Beyond Complexity
Strong passwords alone won’t save you. But they’re still the foundation of good security.
Use a password manager. Let software generate and store complex credentials. You only need to remember one master password. Tools like Bitwarden, 1Password, or KeePass create truly random passwords that don’t follow human patterns.
Enable two-factor authentication everywhere. Even if hackers steal your password, they can’t access your account without the second verification step. Use authenticator apps rather than SMS when possible.

Check if your passwords leaked. Visit Have I Been Pwned and search your email address. The site tells you which services suffered breaches that exposed your credentials. Change those passwords immediately.
Avoid predictable patterns. Don’t just capitalize the first letter and add “!” at the end. Don’t use your birth year or favorite sports team. Hackers know these tricks.
Set regular password updates. Change important credentials annually. System administrators can enforce this through company policies. Yes, it’s annoying. But it works.
Companies and universities need to stop accepting weak passwords. Force users to meet actual security standards. Reject common passwords and dictionary words. Require genuine complexity.
The Threat Keeps Growing
Infostealer developers aren’t slowing down. They’re creating more effective tools that evade detection and steal data faster.
LummaC2’s rapid rise shows how quickly the threat landscape shifts. What worked for security last year might fail this year. Plus, these malware packages are getting bundled and sold to less-skilled criminals, spreading the danger wider.
Meanwhile, users keep choosing terrible passwords. The same five credentials top the stolen-password list year after year. Education clearly isn’t working.
The solution? Remove humans from password creation entirely. Let password managers handle it. Enable automatic breach monitoring. Make two-factor authentication mandatory, not optional.
Your eight-character password with a capital letter and exclamation mark isn’t protecting anything. Hackers cracked that pattern years ago. Time to upgrade your security before the next breach adds your credentials to the leaked-password database.



Comments (0)