Microsoft’s September 2025 security rollout brings substantial changes that directly affect millions of Windows users worldwide. The comprehensive patch bundle addresses 81 vulnerabilities across Windows operating systems, fixing critical remote code execution flaws and two publicly disclosed zero-day vulnerabilities that demand immediate attention from both enterprise administrators and home users.
Critical Security Landscape: Understanding the September Patch Tuesday Scope
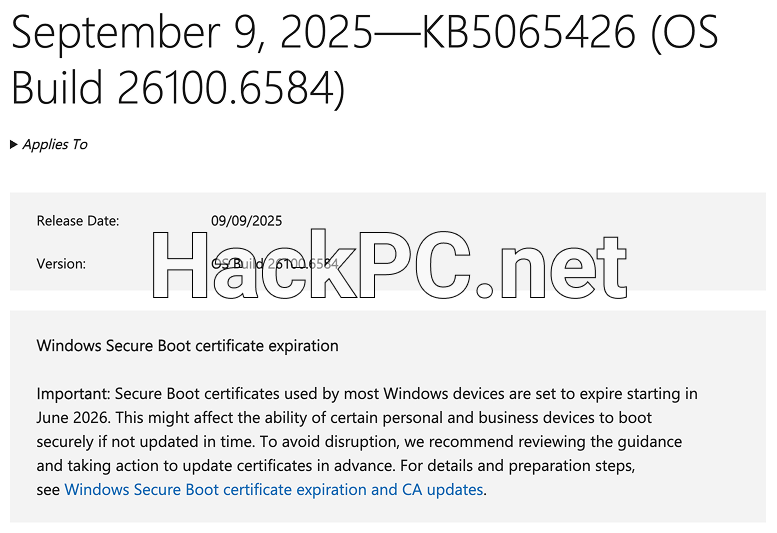
The September 9, 2025 cumulative updates — KB5065426 for Windows 11 24H2, KB5065431 for Windows 11 23H2, and KB5065429 for Windows 10 — represent more than routine maintenance. These patches address nine critical-severity vulnerabilities, including remote code execution threats in Windows Hyper-V, elevation of privilege flaws in Windows NTLM authentication protocols, and information disclosure vulnerabilities affecting the Windows Imaging Component.
According to Microsoft’s Security Response Center, the most concerning vulnerability, CVE-2025-54918, targets Windows NTLM with a CVSS score of 8.8. This critical elevation of privilege vulnerability allows authenticated attackers with minimal privileges to escalate directly to SYSTEM level access through network exploitation. The vulnerability’s “Exploitation More Likely” rating from Microsoft signals genuine risk for unpatched systems, particularly in enterprise environments where NTLM authentication remains widespread despite Microsoft’s ongoing deprecation efforts.
Zero-Day Vulnerabilities: Immediate Threats Requiring Urgent Action
Two publicly disclosed zero-day vulnerabilities elevate this month’s patches from important to critical. CVE-2025-55234, affecting Windows Server Message Block (SMB), enables SMB relay attacks that compromise user credentials without requiring authentication. While Microsoft hasn’t confirmed active exploitation, the public disclosure means threat actors already possess the technical details necessary for weaponization.
The second zero-day, CVE-2024-21907, impacts Newtonsoft.Json libraries embedded within Microsoft SQL Server installations. Specially crafted data passed to JsonConvert.DeserializeObject methods can trigger stack overflow exceptions, potentially causing denial of service conditions across database infrastructure. Tenable’s analysis emphasizes that authenticated attackers can exploit this remotely, making it particularly dangerous for internet-facing SQL Server deployments.
Installation Challenges: Widespread Deployment Issues Affecting Users
The September updates have encountered significant installation problems across diverse Windows environments. Users report multiple error codes including 0x800F081F, 0x800F0991, 0x800F0922, and 0x80071A2D when attempting standard Windows Update installations. These failures particularly affect Windows 11 systems, with KB5065426 repeatedly failing to install through conventional update channels.
System administrators managing enterprise deployments through Windows Server Update Services (WSUS) face additional complications. The combined Servicing Stack Update (SSU) and Latest Cumulative Update (LCU) packaging creates larger-than-normal update files that occasionally timeout during distribution. BleepingComputer reports that successful installation often requires alternative deployment methods, including Microsoft’s Media Creation Tool or Update Assistant for stubborn systems.
Network connectivity issues represent another significant post-installation concern. Multiple users report broken file sharing capabilities after applying KB5065426, with SMB v1 connections failing on NetBIOS over TCP/IP configurations. While SMBv1 remains deprecated and disabled by default in modern Windows installations, legacy enterprise environments still utilizing this protocol face immediate operational disruptions.
SharePoint Server Vulnerabilities: Enterprise Infrastructure Under Attack
Microsoft SharePoint Server faces particular scrutiny this month with CVE-2025-54897 introducing remote code execution risks for on-premises deployments. The vulnerability, carrying a CVSS score of 8.8, allows any authenticated user — without requiring administrative privileges — to execute arbitrary code on vulnerable SharePoint servers through code injection techniques.
CrowdStrike’s analysis reveals that successful exploitation grants attackers complete control over SharePoint content repositories, including file systems and internal configurations. This represents catastrophic risk for organizations storing sensitive documents, intellectual property, or regulatory compliance data within SharePoint infrastructures. The authentication requirement provides minimal protection, as even basic user credentials suffice for exploitation.
Previous SharePoint vulnerabilities from July 2025 demonstrated active exploitation campaigns by Chinese nation-state actors including Linen Typhoon and Violet Typhoon. The rapid adoption of SharePoint exploits by sophisticated threat actors underscores the platform’s attractiveness as an initial access vector for corporate espionage and ransomware deployment.
Hyper-V Critical Vulnerabilities: Virtualization Infrastructure at Risk
Windows Hyper-V virtualization platform received four critical patches addressing remote code execution vulnerabilities. CVE-2025-55224, rated critical with a CVSS score of 7.8, enables attackers to escape guest virtual machine boundaries and execute code directly on host systems. While Microsoft rates exploitation as “Less Likely” due to high attack complexity, successful exploitation compromises entire virtualization infrastructures.
The race condition nature of CVE-2025-55224 requires precise timing but rewards successful attackers with complete host system control. Organizations running multi-tenant virtualization environments face particular risk, as a single compromised guest potentially threatens all co-located virtual machines. Qualys research emphasizes immediate patching for production Hyper-V deployments, particularly those hosting internet-accessible services.
PowerShell Direct Connection Failures: Hotpatch Deployment Complications
Organizations utilizing Microsoft’s Hotpatch technology encounter specific PowerShell Direct (PSDirect) connection failures between host and guest virtual machines. The issue manifests intermittently when patched systems attempt connections to unpatched counterparts, disrupting automated management workflows and configuration deployment pipelines.
Event ID 4625 authentication failures appear in Security Event logs, indicating failed legacy handshake negotiations. While Microsoft released KB5066360 to address these issues, the intermittent nature complicates troubleshooting. Enterprise environments must coordinate simultaneous updates across entire virtualization clusters to maintain PSDirect functionality, significantly increasing deployment complexity and potential downtime windows.
User Account Control Changes: Standard User Workflow Disruptions
The September updates continue addressing UAC prompt issues introduced by August’s security improvements. Non-administrative users encounter unexpected elevation prompts during routine MSI installer operations, including software repairs and per-user configurations. Applications particularly affected include Office Professional Plus 2010 and various Autodesk products including AutoCAD and Civil 3D.
These prompts stem from security vulnerability CVE-2025-50173 mitigations that enforce stricter authentication requirements for Windows Installer operations. While improving security posture, the changes disrupt established workflows where standard users previously performed application maintenance independently. IT departments must either grant additional permissions or implement MSI allowlisting through Group Policy to restore functionality.
Practical Mitigation Strategies: Protecting Systems During Transition
Organizations unable to immediately deploy September patches require compensating controls to minimize exposure. Network segmentation becomes critical, isolating vulnerable systems from internet access and restricting lateral movement opportunities. Disabling unnecessary services, particularly legacy protocols like SMBv1 and NTLM where possible, reduces attack surface significantly.
The SANS Internet Storm Center recommends implementing Enhanced Security Admin Environment (ESAE) architectures to protect privileged accounts from credential theft. Deploying Microsoft Defender for Endpoint or equivalent endpoint detection and response solutions provides visibility into exploitation attempts, even on unpatched systems. Regular monitoring of authentication logs for anomalous NTLM traffic patterns helps identify potential relay attack attempts before credential compromise occurs.
For SharePoint deployments, enabling Antimalware Scan Interface (AMSI) integration provides runtime protection against malicious script execution. Organizations should audit SharePoint farm configurations, removing unnecessary service accounts and implementing least-privilege access models. Web application firewalls configured with SharePoint-specific rulesets offer additional protection layers for internet-facing deployments.
Update Deployment Best Practices: Ensuring Successful Installation
Given widespread installation failures, organizations must adapt deployment strategies for September updates. Testing updates in isolated environments before production deployment remains essential, but additional preparation steps improve success rates. Clearing Windows Update cache folders, running System File Checker (SFC) and Deployment Image Servicing Management (DISM) tools preemptively addresses corruption issues that trigger installation failures.
For persistently failing systems, Microsoft’s Media Creation Tool performs in-place upgrades that bypass problematic update mechanisms while preserving user data and applications. The Update Assistant provides similar functionality with simpler operation for less technical users. Both tools download complete Windows images, ensuring all components receive updates regardless of previous installation states.
Enterprise environments should stagger deployments across organizational units, monitoring early adopters for post-installation issues before broader rollout. Maintaining rollback capabilities through System Restore points or virtual machine snapshots enables rapid recovery from problematic updates. Communication plans preparing users for potential workflow disruptions minimize help desk burden during deployment windows.
Long-Term Security Implications: Windows 10 End of Support Approaching
October 2025 marks Windows 10’s end of support deadline, adding urgency to September’s patches. Systems remaining on Windows 10 after October receive no further security updates unless organizations purchase Extended Security Updates (ESU) licenses. The commercial ESU program, while providing continued patches, represents significant additional costs for organizations with large Windows 10 deployments.
Migration planning to Windows 11 becomes critical for maintaining security posture post-October. Hardware compatibility requirements, particularly Trusted Platform Module (TPM) 2.0 and Secure Boot capabilities, prevent many older systems from upgrading. Organizations must balance hardware refresh costs against ESU licensing fees when determining optimal migration strategies.
Performance Considerations: System Impact Analysis
The September updates introduce noticeable performance implications beyond security improvements. The enhanced SMB auditing capabilities, while valuable for compatibility assessment, generate additional logging overhead that impacts file server performance. Organizations should monitor disk I/O patterns and adjust log rotation policies to prevent storage exhaustion.
Memory utilization increases marginally due to additional security checks in NTLM authentication paths. Systems operating near capacity thresholds may experience degraded response times, particularly during authentication-heavy operations. Performance monitoring during pilot deployments helps identify systems requiring hardware upgrades before production rollout.
Conclusion: Balancing Security Urgency with Operational Stability
September 2025’s Windows security updates present a complex calculus for IT departments and individual users. The combination of critical vulnerabilities, publicly disclosed zero-days, and installation challenges creates competing pressures between immediate security needs and operational stability requirements. Organizations must weigh exploitation risks against potential disruption from problematic updates, developing deployment strategies that minimize both security exposure and business impact.
The approaching Windows 10 end-of-support deadline adds temporal pressure to already complex decision-making. Systems remaining unpatched face genuine compromise risks from increasingly sophisticated threat actors, yet rushed deployments risk operational disruptions from installation failures or post-update issues. Success requires methodical planning, comprehensive testing, and clear communication across technical and business stakeholders.
Microsoft’s continued struggles with update quality, evidenced by persistent installation failures and post-deployment issues, highlight the ongoing challenges of maintaining complex operating system ecosystems. While the company’s rapid response to security vulnerabilities remains commendable, the collateral impact on user productivity and system stability demands equal attention. Organizations must develop robust update management processes that account for both security imperatives and operational realities in an increasingly hostile threat landscape.



Comments (0)