
The internet feels dangerous because it is. Scammers, hackers, and data thieves operate 24/7. Yet most people still treat cybersecurity like an impossible chore.
Here’s the truth: staying safe online doesn’t require a computer science degree. You just need to follow practical steps that actually work. Moreover, many of these protections are completely free.
Let’s break down what actually keeps you secure without requiring hours of your time.
Install Security Updates the Second They Arrive
Software updates aren’t just about new features. In fact, security patches form your strongest defense against technical exploits.
When developers discover a vulnerability, they race to ship a fix. But here’s the catch: by the time that patch arrives, hackers already know about the flaw. Every hour you wait increases your risk.
So train yourself differently. See an update notification? Install it immediately. Don’t click “remind me later” even once.
This single habit blocks most technical attacks before they start.
Weak Passwords Are an Invitation to Get Hacked
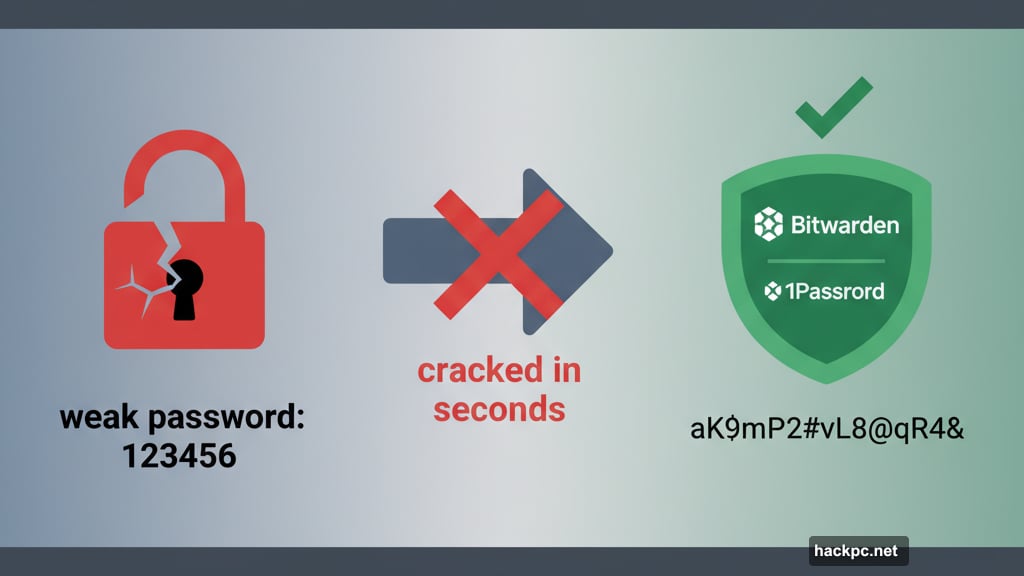
Most data breaches happen because passwords are too easy to guess. Birthdays, pet names, and common phrases all take seconds to crack with automated tools.
Hackers use programs that test millions of combinations per second. Short passwords fall fast. Even random characters won’t save you if the string is only six characters long.
You need passwords that are both long and meaningless. That sounds impossible to remember, right?
Enter password managers. These apps generate unbreakable passwords, store them securely, and fill them in automatically. You only remember one master password that unlocks everything else.
Popular options like Bitwarden and 1Password work seamlessly across devices. Plus, they’re far more convenient than trying to remember dozens of complex passwords yourself.
Two-Factor Authentication Stops Hackers Cold
Strong passwords aren’t enough anymore. Data breaches expose even the best credentials regularly through no fault of your own.
That’s why two-factor authentication (2FA) matters. It adds a second verification step that hackers can’t bypass even if they steal your password.
Most people think 2FA means grabbing your phone to enter a code. But passkeys now offer a better option.
Passkeys use asymmetric encryption between your device and the service. You don’t enter anything – the system confirms your identity automatically. It’s faster for you and leaves nothing for criminals to steal.
Major platforms like Google and Apple already support passkeys. Enable them wherever you can.
Ransomware Can’t Touch You With Proper Backups
Ransomware attacks lock your files until you pay a ransom. These scams are exploding because they work – desperate victims often pay up.
But there’s a simple counter: restore everything from backup. Ransomware becomes worthless if you can wipe your system clean and reload fresh copies of all your files.
Security experts recommend the 3-2-1 rule. Keep three separate backups on two different storage types, with at least one physically distant from your main system.
For example: one backup on another device at home, one in cloud storage, and one on a portable hard drive you keep elsewhere.
Automatic backup services handle this for you at set intervals. Set it up once, then forget about it until you need it.
Social Engineering Attacks Exploit Human Nature
Here’s a surprise: most cyber attacks don’t require technical skills. Scammers just trick you into handing over information willingly.
These “social engineering” attacks use fear and urgency to bypass your critical thinking. A fake email from your bank demands your password to fix a serious problem. A text warns about a speeding ticket you never got. A receipt arrives for a subscription you didn’t buy.
The approach varies but the psychology stays the same. Create panic, offer a solution, collect your data.
So take a breath every time you receive an alarming message. Then investigate before you act.
Look up the sender’s email address. Check if the visual design matches the real company. Ask yourself if the scenario makes any sense at all.
This free phishing quiz from Google teaches you to spot fakes. It’s challenging but extremely educational.
Never Click Links Without Checking Them First
Some scams don’t want your information directly. Instead, they trick you into clicking malicious links that secretly install malware on your device.
Keyloggers watch you type passwords. Ransomware corrupts your files. Other programs spy on everything you do online.
Fortunately, you can check suspicious links before clicking. Copy the link without opening it, then paste it into a URL checker like NordVPN‘s free tool. These services tell you if a link connects to known malware domains.
You can also hover over any link to see where it actually goes. Look at the bottom-left corner of your browser – the real destination appears there.
If an email claims to be from your bank but links somewhere else entirely, that’s a massive red flag.
Your Social Media Posts Help Scammers Target You
Social media trained us to broadcast personal details constantly. That habit supercharges the scam economy.
Posting your kids’ names, vacation dates, or childhood memories seems harmless. But every detail you share makes it easier for strangers to manipulate you.
Take “grandparent scams” as an example. Criminals contact seniors pretending to be their grandchild in crisis. They claim they need money urgently for an emergency.
The more information they gather from social media beforehand, the more convincing their story becomes.
Oversharing also makes weak passwords even weaker. Public information helps criminals guess your credentials or answer your security questions.
So think twice before you engage with that Facebook quiz asking for your childhood pet’s name.
VPNs Hide Your Digital Footprint
Virtual private networks (VPNs) aren’t magic security shields. They can’t protect you from weak passwords or malicious links.
But they do one thing extremely well: hide your identity online.
A VPN replaces your real IP address with one belonging to a server it owns. The VPN server handles all your internet traffic while encrypting everything between it and your device.
This means nobody can connect your online actions to your real identity. Data brokers can’t track which websites you visit. Advertisers can’t build profiles on you. Governments can’t monitor your activity.
VPNs also protect you on public Wi-Fi. Even if a hacker tricks you with a fake network, they can’t do much without your real IP address.
Top VPNs like Proton VPN include ad blockers that stop cookies and tracking pixels from latching onto you.
You won’t be invulnerable with a VPN. But you’ll be far safer and more private than without one.
Antivirus Software Catches Threats Early
The best time to stop malware is when it first arrives on your system. Suspicious downloads can carry hidden programs that install themselves without your knowledge.
Quality antivirus software scans files as you download them. It catches obvious malware immediately and quarantines suspicious files until it confirms they’re safe.
Modern antivirus apps use machine learning to identify common malware patterns. This lets them catch brand-new viruses that behave like old ones.
But what about threats already on your computer? Regular virus scans check your entire system for unwanted programs hiding as legitimate files.
Windows computers come with Windows Defender built in. That’s enough for basic protection. However, I still recommend at least one dedicated anti-malware program on any device.
Email Maskers and Private Search Keep Your Data Close
The less personal information you put online, the safer you are. That’s obvious with social media. But your data spreads through other channels too.
Every time you create an online account, you typically need an email address. That contact information then floats around online indefinitely, increasing your exposure to scams and spam.
Email maskers solve this problem. Services like SimpleLogin give you fake addresses that forward messages to your real inbox. You stay protected while still receiving important communications.
Search engines are another data leak. Google builds detailed profiles by tracking your search terms. Then it sells that information to advertisers.
Private search engines like DuckDuckGo don’t track anything. They make money from non-targeted ads on results pages instead of selling your data.
Data Removal Services Clean Up Your Trail
Bad news: if you’ve used the internet in the last decade, data brokers probably have files on you. These companies make money hoarding and selling personal information.
These brokers range from public people-search sites to private backend dealers. They’re poorly regulated and careless about security. The longer they hold your data, the more likely it leaks.
Good news: most brokers must delete your data if you request it. That’s the law in many places.
Bad news again: hundreds of brokers might have your information. Each one makes opting out deliberately difficult.
Data removal services like DeleteMe and Incogni handle this tedious process for you. They contact brokers on your behalf and verify your data gets removed.
It’s not cheap. But neither is dealing with identity theft.
Physical Security Still Matters in a Digital World
Many online threats depend on old-fashioned tactics. Physical infiltration and theft still compromise cybersecurity regularly.
Leaving your laptop unattended in public? Someone might insert a flash drive that loads malware. Unlocking your phone in a crowded bar? A thief might watch your pattern then steal your device.
One criminal in Minneapolis made a practice of this. He’d watch people unlock their phones, steal those phones, then unlock them himself using the pattern he’d memorized.
I’m not suggesting you become paranoid. Just use the same caution you’d apply to protecting your car.
Lock your phone with biometric authentication so only you can open it. Never leave devices lying around if they can access your accounts. At work, don’t let anyone into secure areas without proper credentials.
Simple physical security habits prevent problems that no software can fix.
Small Steps Add Up to Real Protection
You don’t need to implement everything at once. Even focusing on one or two of these steps makes you substantially safer online.
Start with what feels most urgent for your situation. Maybe that’s enabling 2FA on your most important accounts. Maybe it’s finally setting up automatic backups.
The key is actually doing something instead of feeling overwhelmed by the entire list.
Cybercriminals count on people being too busy or too confused to protect themselves. Prove them wrong by taking just one small step today.



Comments (0)