
A malicious code package just compromised thousands of WhatsApp accounts. Worse yet, removing the infected software doesn’t fix the problem.
Security researchers discovered the attack hiding in plain sight on one of the world’s most popular developer platforms. Plus, it had been stealing messages and contacts for six months before anyone noticed.
Hackers Weaponized a Trusted Developer Tool
The attack targeted developers using Node Package Manager (NPM), a massive public registry hosting JavaScript code packages. Millions of developers rely on NPM to build web and mobile applications.
Cybersecurity firm Koi Security found the malicious package masquerading as “lotusbail.” It pretended to be a legitimate fork of WhiskeySockets Baileys, a popular open source library that lets developers connect applications to WhatsApp Web.
Here’s the clever part. The malicious version included all the same functionality as the real project. So developers using it wouldn’t immediately notice anything wrong. Their WhatsApp integrations worked perfectly.
But behind the scenes, the code was stealing everything.

Every Message Flows Through the Attack
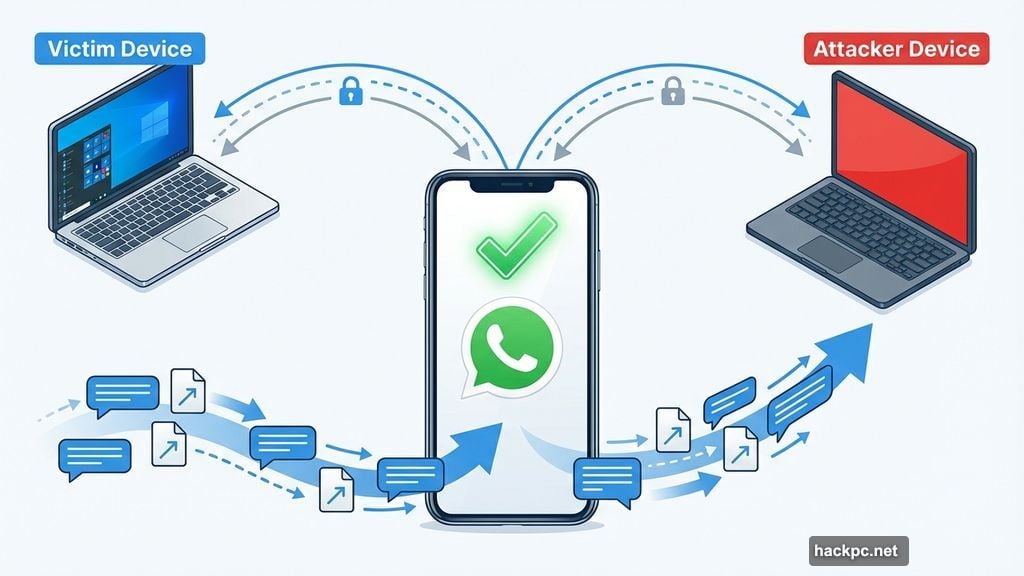
The malware wraps itself around WhatsApp’s communication channel. That means it sees every message, contact, photo, and document passing through the connection.
“When you authenticate, the wrapper captures your credentials,” Koi Security explained in their report. “When messages arrive, it intercepts them. When you send messages, it records them.”
All that stolen data gets sent to a third-party server controlled by the attackers. So they collect authentication tokens, session keys, messages, contacts, and media files in real time.
But the attack gets worse from there.
The Malware Links Attackers’ Devices Permanently
Most alarming is how the package exploits WhatsApp’s companion device pairing feature. It secretly links the attacker’s device to the victim’s WhatsApp account.

That’s a huge problem. Even after developers discover and remove the malicious package, their WhatsApp accounts remain compromised. The attacker’s device stays connected until the victim manually disconnects it through WhatsApp settings.
Most victims won’t realize they need to take that extra step. So attackers maintain persistent access to accounts long after the initial infection.
The package sat on NPM for at least six months. During that time, it racked up more than 56,000 downloads. That’s potentially thousands of compromised WhatsApp accounts.
NPM Gets Targeted Constantly
This attack highlights a persistent problem with public code repositories. NPM hosts hundreds of thousands of packages that developers download and integrate into their projects.
But anyone can publish packages to NPM. Attackers regularly upload malicious code disguised as legitimate tools. They use tactics like typosquatting (misspelling popular package names) or creating forks of trusted projects.
Developers often grab packages without carefully vetting them first. Popular packages with thousands of downloads seem trustworthy. But as this attack proves, download counts don’t guarantee safety.
Moreover, NPM’s scale makes thorough security review nearly impossible. Thousands of new packages get published daily. Malicious code can sit undetected for months while racking up downloads.
How to Protect Your WhatsApp Account
If you’re a developer who might have installed lotusbail, take action immediately.
First, check your linked devices. Open WhatsApp on your phone. Go to Settings, then Linked Devices. Remove any devices you don’t recognize. This disconnects the attacker’s access.
Second, review your NPM dependencies carefully. Check your project’s package.json file for lotusbail or any suspicious Baileys forks. Remove them and reinstall from the legitimate WhiskeySockets repository.
Third, change your authentication credentials. Generate new API keys and tokens for any WhatsApp integrations. This invalidates the stolen credentials attackers collected.
For all developers, verify package sources before installation. Check the package’s npm page, GitHub repository, and recent activity. Be suspicious of packages with similar names to popular projects.
Finally, use tools like npm audit to scan your dependencies for known vulnerabilities. While it won’t catch every malicious package, it helps identify obvious threats.
The Real Cost of Open Source Trust
This attack exploits something fundamental about modern software development. Developers rely on open source packages to build applications faster. But that efficiency requires trusting code written by strangers.
NPM’s open model powers incredible innovation. But it also creates opportunities for attackers. And the consequences reach far beyond developer machines. When malicious packages target messaging apps, they compromise user privacy at scale.
The solution isn’t avoiding NPM or open source software. But developers need to treat every dependency as a potential security risk. That means verification, code review, and constant vigilance.
Your next npm install could hijack more than just your project. It might steal your conversations too.



Comments (0)