
WatchGuard just patched a nightmare vulnerability. The flaw let attackers take complete control of firewalls without any authentication required.
This isn’t some theoretical exploit. It’s exactly the kind of security hole ransomware gangs dream about. Plus, it affects internet-facing devices that protect entire networks.
Here’s what happened and how to protect your infrastructure.
The Vulnerability That Should Terrify Network Admins
CVE-2025-9242 earned a critical severity score of 9.3 out of 10. That’s as serious as it gets.
The flaw exists in WatchGuard Fireware, the operating system running on WatchGuard’s security appliances. Specifically, it’s an out-of-bounds write vulnerability. In plain English? Attackers can inject and execute malicious code remotely.
No password needed. No authentication required. Just direct access to your firewall’s guts.
The vulnerability affects VPN configurations using IKEv2 protocol with dynamic gateway peers. So both mobile user VPNs and branch office VPNs were exposed. Anyone running these configurations was vulnerable until they patched.
Why Ransomware Groups Love These Flaws
Security researchers at watchTowr didn’t mince words. They called this vulnerability a gift to ransomware operators.
Think about it. Firewalls sit at the network perimeter. They see and control all internet traffic flowing in and out. Compromise a firewall, and you’ve got the keys to the kingdom.
Ransomware gangs specifically target these chokepoints. They also love VPN gateways, RDP services, and remote management interfaces. Why? Because one vulnerability gives them access to hundreds or thousands of devices behind that gateway.
Moreover, attacking firewalls lets criminals monitor traffic, steal credentials, and move laterally across networks. They can disable security controls before launching their encryption attacks. That’s why firewall vulnerabilities command premium prices on dark web forums.
This particular flaw made life even easier. Attackers didn’t need stolen credentials or phishing success. Just send malicious packets to an exposed device and execute code. Simple. Devastating.
Which Versions Got Hit
WatchGuard released patches for multiple affected versions. Here’s the damage:
Vulnerable versions:
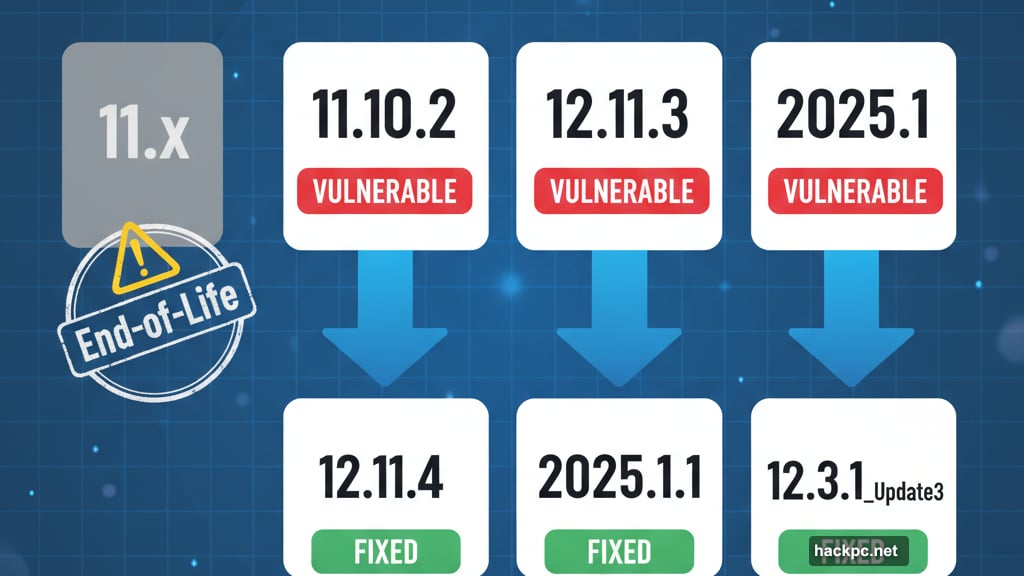
- 11.10.2 through 11.12.4_Update 1
- 12.0 through 12.11.3
- 2025.1
Fixed versions:
- 2025.1.1 addresses the 2025.1 branch
- 12.11.4 fixes version 12.x devices
- 12.3.1_Update3 (build B722811) patches the FIPS-certified release
- 12.5.13 covers T15 and T35 models
- Version 11.x reached end-of-life (no patch available)
That last point matters. If you’re still running version 11.x, you’re out of luck. WatchGuard won’t provide security updates. So you need to upgrade hardware or migrate to supported software immediately.
How to Protect Your Network Right Now
First, patch everything. Download the appropriate fixed version for your WatchGuard devices and apply it immediately. This vulnerability is too critical to wait for your next maintenance window.
Second, limit internet exposure. Far too many organizations leave management interfaces accessible from the public internet. That’s asking for trouble.
Only essential devices should accept connections from outside your network. Everything else belongs on your local network behind proper access controls. Use VPNs or jump boxes to reach internal management interfaces.
Third, review your VPN configurations. If you’re using IKEv2 with dynamic gateway peers, audit those connections carefully. Ensure you’ve patched all affected devices.
Fourth, monitor for suspicious activity. Check firewall logs for unusual connection attempts or unexpected configuration changes. Look for failed authentication attempts that suddenly stopped (possibly because attackers found this vulnerability).
Finally, train your staff. Phishing and social engineering remain primary attack vectors even when vulnerabilities exist. Your employees need to recognize suspicious emails, links, and requests for credentials.
Beyond This Specific Flaw
This incident highlights broader security principles that apply beyond WatchGuard devices.
Ransomware operators constantly probe for vulnerabilities in network perimeter devices. They target Cisco firewalls, Fortinet appliances, Palo Alto Networks devices, and others. No vendor is immune.
So organizations need defense-in-depth strategies. Don’t rely solely on firewall security. Implement network segmentation so compromising one device doesn’t expose everything. Use endpoint detection and response tools to catch threats that bypass perimeter defenses.
Also, maintain current inventory of all network devices and their software versions. Too many companies run outdated equipment they forgot about. Those orphaned devices become easy targets when critical vulnerabilities emerge.
Backup strategies matter too. Ransomware encrypts backups along with production systems. Store backup copies offline or in immutable storage that attackers can’t touch. Test restoration procedures regularly to ensure backups actually work when needed.
The Bigger Picture on Gateway Security
Network perimeter security has never been more challenging. The shift to remote work expanded attack surfaces dramatically. Cloud migrations added complexity. IoT devices multiplied entry points.
Traditional castle-and-moat security doesn’t work anymore. Businesses need zero trust architectures that verify every connection regardless of source. Assume breach mentality means planning for compromise rather than hoping to prevent it.
That said, firewall and VPN security still matters enormously. These devices remain critical chokepoints. Keeping them patched and properly configured prevents most opportunistic attacks.
Critical vulnerabilities like CVE-2025-9242 remind us why patch management deserves investment and attention. Organizations that delay updates or skip patches eventually pay the price through ransomware infections, data breaches, or worse.
The choice is simple. Spend time patching now. Or spend weeks recovering from compromise later while explaining to customers why their data leaked.
Update your WatchGuard devices today. Check other network equipment for pending patches. Lock down internet-accessible management interfaces. Your future self will thank you.



Comments (0)