
Dutch authorities just seized a Windscribe VPN server without warning. No warrant. No explanation. Just walked in and pulled it from the rack.
But here’s the twist. They won’t find anything useful on it. In fact, Windscribe CEO Yegor Sak told them exactly that before they took it. The server runs entirely on RAM. Once disconnected, all data vanishes instantly.
This marks the second time in three years that authorities have challenged Windscribe’s no-logs policy in a real-world legal scenario. So far, the company’s track record remains spotless.
What Actually Happened
Friday morning, Dutch authorities showed up at a data center and seized one of Windscribe’s servers. They claimed it was needed for an active investigation. That’s all they said.
No warrant. No court order. Just a verbal promise to return the server after they “fully analyze it.”
Sak explained to CNET that authorities possibly wanted to perform a RAM dump. This technique captures a server’s active memory before data disappears. But even if they succeeded, they’d find nothing valuable.
Why? Because Windscribe uses RAM-only servers. These systems run on volatile memory that erases completely when power cuts or network disconnects. The moment authorities unplugged that server, any data in memory vanished.
“The only thing the authorities will find is a stock Ubuntu install,” Windscribe announced on X.
RAM-Only Architecture Changes Everything
Most traditional servers write data to hard disks. This creates permanent records that survive reboots and power failures. Great for reliability. Terrible for privacy.
RAM-only servers work differently. They store everything in temporary memory. No hard drives. No permanent storage. When the server loses power or reboots, everything disappears.
Think of it like writing on a whiteboard versus carving into stone. The whiteboard erases completely. The stone lasts forever.
This is why we always prioritize VPNs with RAM-only infrastructure when testing. It’s not just marketing speak. It’s genuine technical protection against exactly this scenario.
Moreover, Windscribe doesn’t log user activity even when servers are running. No source IPs. No connection timestamps. No browsing history. Without logs, there’s nothing to seize in the first place.
This Isn’t Windscribe’s First Test
Back in 2023, Greek authorities charged Sak personally with “illegal access to information system.” Someone had used a Windscribe server to breach a Greek website and send spam emails.
Greek police wanted logs. They wanted to identify the actual perpetrator. So they went after Windscribe’s CEO instead.
The case dragged through courts for months. But ultimately, prosecutors dismissed all charges. Why? Because Windscribe proved it had nothing to hand over.
“You cannot hand over what you do not have,” Sak wrote in a blog post after the case closed.
That Greek case tested Windscribe’s no-logs policy under real legal pressure. The company passed. Now Dutch authorities are running the same test again.
Why Third-Party Audits Matter
No-logs claims sound great in theory. But how do you verify them? You can’t just take a company’s word for it.
This is where independent audits become crucial. Third-party security firms examine a VPN’s infrastructure, code, and policies. They verify whether the company actually does what it claims.
Windscribe has been audited regularly since 2021. The most recent audit, published in summer 2024, examined the company’s FreshScribe VPN infrastructure. Auditors confirmed that Windscribe’s systems matched its privacy promises.
However, audits aren’t perfect. They’re snapshots in time. Companies know when auditors are coming. So they can prepare.
Real-world legal cases like this Dutch server seizure provide even stronger evidence. Authorities don’t announce their raids. They don’t give companies time to clean up. They just show up and take what they want.
So far, Windscribe has passed every unexpected test.
What Dutch Authorities Will Actually Find
Windscribe runs a transparency report showing every legal request it receives. The counter currently shows zero complied requests “due to lack of relevant data.”
That’s not because Windscribe refuses to cooperate. It’s because they genuinely have nothing useful to share.
“We get a handful of law enforcement requests every month,” Windscribe explained on X. “And each time we tell them we have no logs. This time they didn’t ask, they just snatched the server from the rack to look for the logs themselves.”
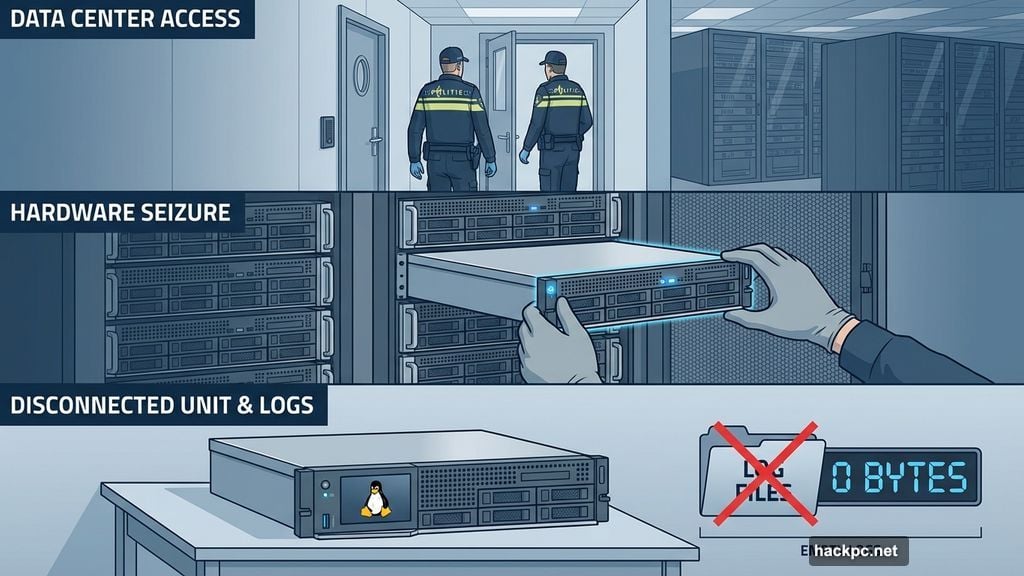
What will Dutch forensic teams discover when they analyze that server? A clean Ubuntu installation. No user data. No connection logs. No browsing history.
Plus, even if they managed a successful RAM dump before disconnecting the server, they’d find only temporary connection states. No identifying information. No historical records.
The whole thing is like raiding a library looking for specific books, only to discover the shelves burn clean every night. You might know books existed. But you can’t prove which ones or who read them.
Server Seizures Are Getting Common
This incident highlights a growing trend. Governments increasingly target VPN infrastructure directly when traditional legal requests fail.
In 2021, Russian authorities seized ExpressVPN servers looking for logs. They found nothing. The servers were RAM-only.
In 2022, Ukrainian authorities requested data from NordVPN. The company had nothing to provide. No logs existed.
Now Dutch authorities are trying the same approach with Windscribe. They’ll likely reach the same conclusion: you can’t extract data that never existed.
This is why server infrastructure matters more than marketing claims. When authorities show up with or without warrants, your VPN’s technical architecture determines whether your privacy survives.
The Bigger Worry
Windscribe raised an interesting point in their X announcement. They said “the bigger worry” isn’t about user data on seized servers.
The real concern? Governments circumventing legal processes entirely. No warrants. No judicial oversight. Just taking hardware because they can.
If authorities can seize servers without warrants, what other privacy protections can they ignore? Where does this trend stop?
For now, Windscribe users remain protected. The seized server contained nothing useful. The company’s no-logs policy held up under yet another real-world test.
But the incident reveals how aggressive some governments are becoming about accessing VPN data. Even when companies prove repeatedly they have nothing to share.
Your VPN choice matters. Not just because of marketing promises. But because of how systems actually perform when authorities come knocking. Windscribe just proved its systems work exactly as advertised. Again.



Comments (0)