
A small checkmark carries a lot of weight. When Google tags a VPN as “verified,” it feels like someone credible has done the hard work for you.
For most people, that’s exactly how it lands. Very few users can actually audit what a VPN does under the hood. Reading source code, inspecting traffic, or working through a formal security assessment isn’t realistic for everyday shoppers. So visible signals — badges, rankings, reviews — end up doing most of the work.
But here’s the problem. Google’s verified badge sounds broader and more final than it actually is. And when the product you’re choosing is supposed to protect your privacy, that gap really matters.
What Google’s Verification Badge Actually Checks
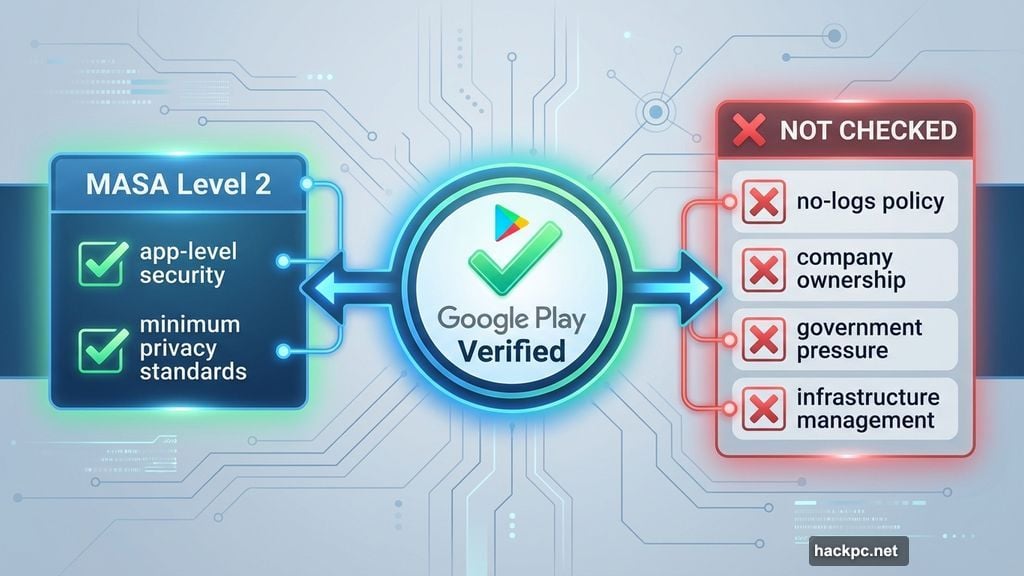
To earn the verified badge on Google Play, a VPN must complete a Mobile Application Security Assessment, known as MASA, at Level 2. That’s a formal review against Google’s minimum security and privacy standards.
There’s also a baseline threshold to clear. Apps need at least 10,000 installs, a solid number of reviews, and an established track record on the Play Store before they’re even considered. Early examples of apps receiving the badge include NordVPN, hide.me, and Aloha Browser.
On the surface, that sounds reasonable. The badge signals that an app has gone further than most listings and shown willingness to meet platform rules.
But here’s what MASA doesn’t cover. It checks app-level security practices, not the deeper questions that actually define whether a VPN deserves your trust. It can’t confirm whether a provider truly keeps no logs, who ultimately owns the company, how the infrastructure is managed, or what pressures the service might face from governments or business partners. Those details tend to matter most — and they sit largely outside what any platform badge can realistically verify.
Verified at One Moment, Not Forever
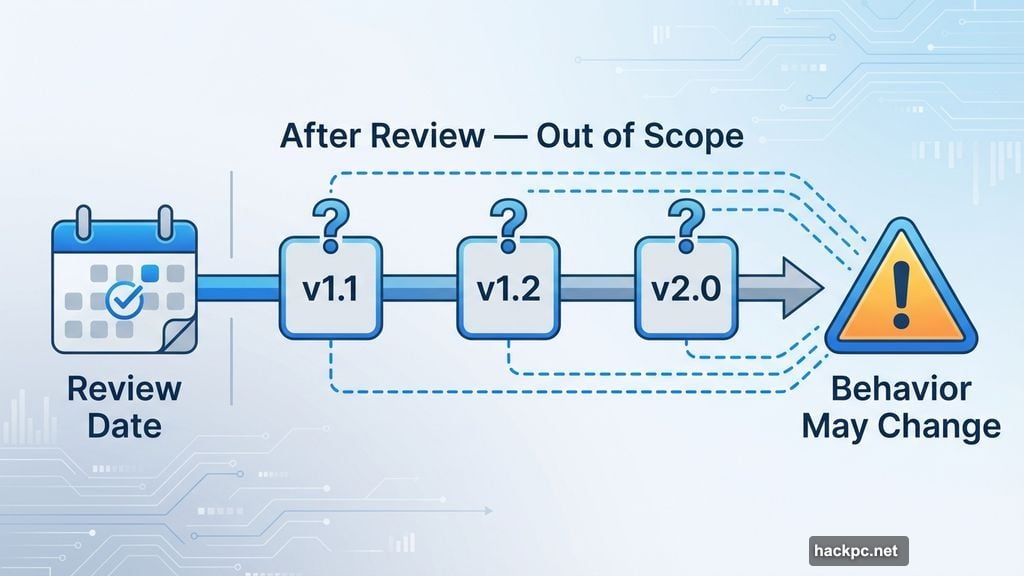
Platform reviews are snapshots, not ongoing surveillance. When Google reviews an app on the Play Store or Chrome Web Store, they evaluate a specific version at a specific point in time.
What happens after that review is largely out of scope. A verified badge means an app met certain standards when it went through the process. It doesn’t mean the app is being continuously monitored. And it certainly doesn’t mean its behavior will never change.
So the badge reflects compliance at the time of review. Not a permanent seal of good behavior.
That distinction matters more for VPNs than it does for, say, a to-do list app.
Why VPNs Face a Higher Privacy Standard
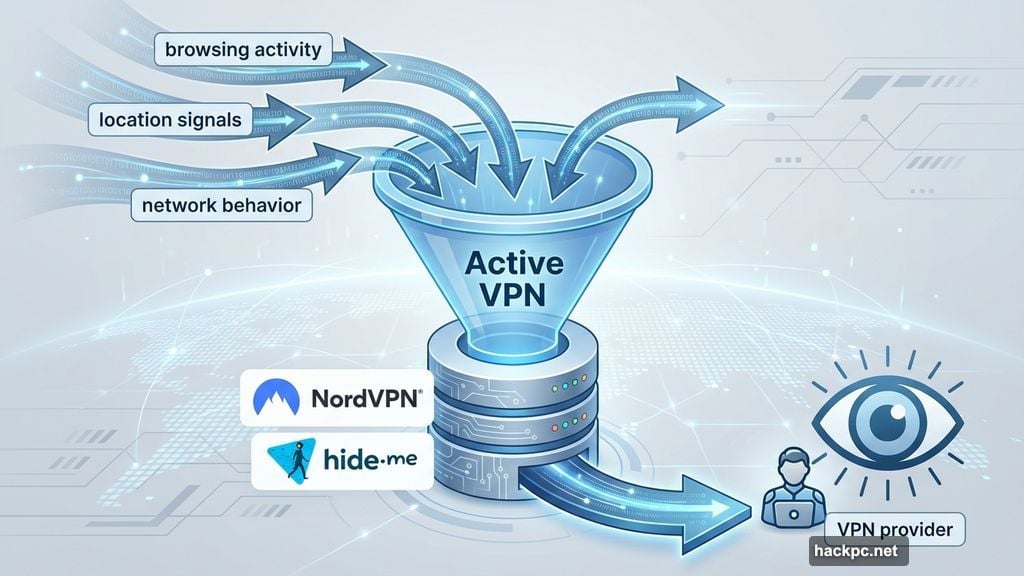
When a VPN is active, all of your internet traffic flows through it. That gives the service visibility into your browsing activity, location signals, and network behavior that almost no other app can see.
People turn to VPNs specifically because they want to avoid tracking, stay safe on public Wi-Fi, or keep their activity private from service providers or governments. In those situations, the VPN is being trusted with data you wouldn’t willingly hand over anywhere else.
That’s exactly why trust failures hit harder here. A VPN doesn’t expose a small slice of your data — it can expose everything in one sweep. If the service logs your activity or leaks your traffic, the damage is broad and immediate.
So while a badge might be a perfectly fine shortcut for evaluating a weather app, it’s not enough when the product itself is a privacy tool.
A Real-World Warning From Browser Extensions
Research from KOI Security offers a useful reality check — and while it focused on browser extensions rather than mobile VPN apps, the lesson applies directly.
KOI documented how Urban VPN, a browser extension with millions of users, passed Google’s Chrome Web Store verification and earned a badge. It presented itself as a privacy tool. Behind the scenes, it was collecting sensitive user data — including AI chat conversations — and sending that data to third parties for profit. This happened regardless of whether the VPN feature was even turned on.
That gap is the core issue. A product branded around privacy was doing the opposite, while a badge implied it had been vetted and could be trusted. For many users, that checkmark likely carried more weight than anything buried in the fine print.
This isn’t a claim that all verified mobile VPN apps behave the same way. The bigger point is that platform reviews tend to focus on what’s easiest to verify, not necessarily what users actually need to know. Technical compliance and deeper accountability are not the same thing.
What Actually Signals VPN Trustworthiness
So if the badge isn’t enough, what should you look for? Here’s what carries real weight.
Independent security audits with published results. When a VPN hires an outside firm to audit its no-logs claims and publishes the findings, that’s meaningful. It opens the service to external scrutiny rather than just self-reporting. Look for auditors with genuine reputations and reports you can actually read.
Clear ownership and a transparent business model. Incentives shape behavior. A VPN that’s clear about who owns it, where it’s based, and how it makes money is easier to trust than one that obscures those details. Some VPN companies are owned by larger conglomerates with their own data interests — that’s worth knowing before you sign up.
Jurisdiction and legal exposure. Where a VPN company is based determines what laws apply to it. A provider headquartered in a country with aggressive data retention requirements faces very different pressures than one in a jurisdiction with strong privacy protections. That context matters when evaluating what “no logs” actually means in practice.
Update history and changelog transparency. VPNs update regularly. How a company communicates those updates tells you a lot. Quiet changes to data collection or core app behavior are a significant red flag for a product built on trust. Transparency here isn’t optional — it’s part of the deal.
A clean track record. Has this VPN had privacy incidents that only came to light because researchers or journalists dug for them? Or does the company proactively disclose problems and fix them? History matters more than marketing.
The Badge Is a Starting Point, Not a Finish Line
None of this means Google’s verified badge is worthless. It tells you that a VPN cleared a baseline review and met minimum platform standards. That’s not nothing. It shows some engagement with platform rules and a basic level of effort.
But it was never designed to answer the questions that matter most for a privacy tool. And treating it as a final answer puts real trust in the wrong place.
Before downloading any VPN, look beyond the badge. Check for third-party no-logs audits. Investigate who owns the company. Understand the jurisdiction. Read the privacy policy — actually read it, not just the summary. And search for any incidents that required outside researchers to uncover.
A checkmark is a starting point. What you find after that determines whether the VPN actually deserves your trust.



Comments (0)