Your ISP knows every website you visit. Marketing companies track your browsing habits across thousands of sites. Hackers on public WiFi can intercept your passwords in seconds. These aren’t hypothetical scenarios—they happen millions of times daily to unprotected internet users. The solution isn’t complicated, but configuring it correctly makes all the difference between basic protection and bulletproof privacy.
Proton VPN emerged from the same Swiss team that revolutionized email encryption with Proton Mail, bringing CERN-level security expertise to consumer VPN services. Unlike typical VPN providers that promise privacy while secretly logging your data, Proton operates under Switzerland’s fortress-like privacy laws with fully open-source, independently audited code. This comprehensive guide reveals exactly how to configure Proton VPN’s advanced features for maximum data protection, turning you from an easy target into a digital ghost.
Understanding Proton VPN’s Security Architecture
Before diving into configuration, it’s crucial to understand what makes Proton VPN particularly robust for data protection. Based in Switzerland, outside the EU and major surveillance alliances, the service operates under some of the world’s strictest privacy laws. The company maintains a verified no-logs policy, meaning your browsing activity and IP address remain completely private.
The foundation of Proton VPN’s security lies in its military-grade encryption standards. All network traffic is protected using either AES-256 or ChaCha20 encryption, combined with secure VPN protocols like WireGuard and OpenVPN. This multi-layered approach ensures your data remains protected even against sophisticated threats.
Initial Setup and Account Security Configuration
Step 1: Choosing the Right Subscription Plan
While Proton VPN offers a free plan with unlimited bandwidth—unique among premium VPN providers—serious privacy users should consider the Plus or Unlimited plans. These paid tiers unlock essential security features including:
- NetShield Ad-blocker for DNS filtering and malware protection
- Secure Core servers for double VPN protection
- Access to over 120 countries with high-speed connections
- Support for up to 10 simultaneous device connections
Step 2: Enabling Two-Factor Authentication
Your first priority after creating an account should be securing it with two-factor authentication. This additional layer prevents unauthorized access even if your password is compromised. Navigate to your Proton account settings and enable 2FA using an authenticator app rather than SMS for maximum security.
Step 3: Download and Install Open-Source Apps
Proton VPN’s applications are fully open-source and regularly audited by independent security professionals. Download the official app for your device directly from Proton’s website to avoid potentially compromised versions. The service supports Windows, macOS, Linux, Android, iOS, and even has browser extensions for Chrome and Firefox.
Optimal Protocol Selection for Maximum Protection
Understanding VPN Protocol Options
The choice of VPN protocol significantly impacts both your security and connection performance. Proton VPN offers several options, each with specific advantages:
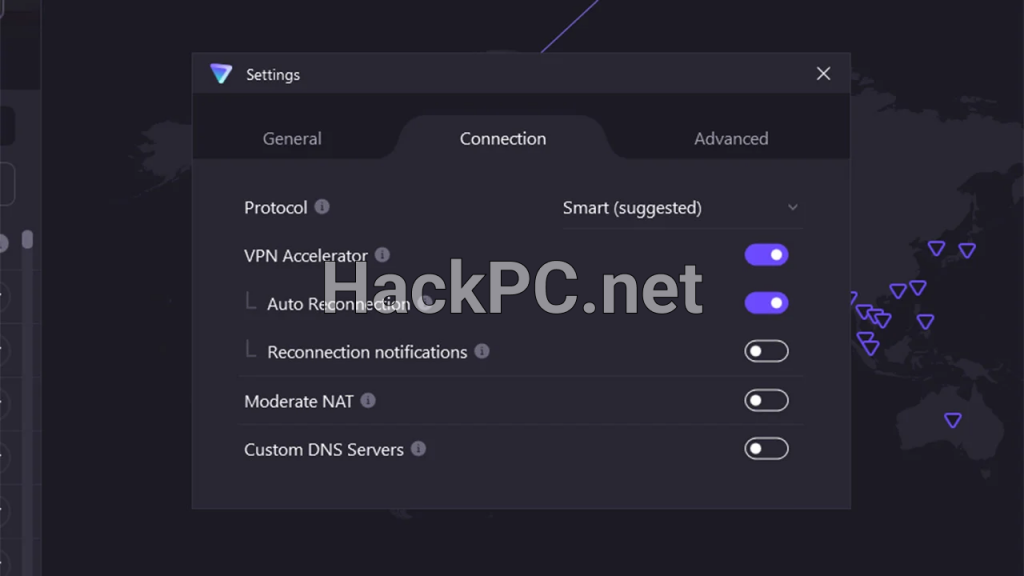
WireGuard Protocol (Recommended) The newest and most efficient protocol, WireGuard uses state-of-the-art cryptographic primitives including ChaCha20 and Curve25519. It provides the best combination of speed and security for most users. Enable WireGuard by navigating to Settings → Connection → Protocol and selecting WireGuard UDP for optimal performance.
OpenVPN (Alternative for Compatibility) With over 20 years of proven security, OpenVPN remains highly reliable. Proton VPN implements it with RSA-4096 key exchange and HMAC SHA-384 authentication. Choose OpenVPN TCP when you need to bypass restrictive firewalls that block UDP traffic.
Stealth Protocol (For Censorship Circumvention) Proton’s proprietary Stealth protocol disguises VPN traffic as regular HTTPS connections, essential for bypassing deep packet inspection in restrictive networks or countries with heavy internet censorship. While slower than other protocols, it’s invaluable when other options fail.
Configuring Smart Protocol Selection
For users who prefer automated optimization, enable Smart Protocol in your settings. This feature intelligently probes networks to discover the best VPN protocol configuration for your current connection, automatically switching between protocols to maintain connectivity and performance.
Essential Security Features You Must Enable
1. Kill Switch Configuration
The kill switch is non-negotiable for serious privacy protection. Proton VPN offers two versions:
Standard Kill Switch: Temporarily disconnects internet access if the VPN connection drops unexpectedly, preventing IP address leaks.
Advanced Kill Switch: Only allows internet access through the VPN, even when the application is closed. This provides maximum protection but requires manual disabling for non-VPN browsing.
To enable: Click the Kill Switch icon on the main screen and select your preferred version. Most users should start with Standard and upgrade to Advanced once comfortable with VPN-only browsing.
2. NetShield Ad-blocker Activation
Available on paid plans, NetShield provides comprehensive DNS filtering that blocks ads, trackers, and malicious scripts. Recent updates in 2025 expanded its capabilities to include phishing protection, blocking almost all known phishing domains automatically.
Configure NetShield by selecting from three protection levels:
- Basic: Blocks malware only
- Standard: Blocks malware and ads
- Advanced: Blocks malware, ads, and trackers
For maximum protection, always use the Advanced setting unless specific websites require tracker functionality.
3. DNS Leak Protection
Proton VPN automatically routes all DNS queries through its encrypted tunnel, preventing your ISP from monitoring your browsing activity. This feature works automatically, but verify it’s functioning by visiting dnsleaktest.com while connected to the VPN.
4. IPv6 Leak Protection
While connected to Proton VPN, IPv6 traffic is automatically blocked to prevent potential leaks. This ensures all your internet traffic passes through the secure IPv4 tunnel, maintaining complete privacy even on networks that support IPv6.
Advanced Privacy Configuration with Secure Core
Understanding Multi-Hop Architecture
Secure Core represents Proton VPN’s implementation of double VPN or multi-hop technology. When enabled, your traffic routes through two servers: first through hardened servers in privacy-friendly countries (Switzerland, Iceland, or Sweden), then to your chosen exit location.
This architecture defends against sophisticated network-based attacks and timing correlation attacks. Even if an adversary monitors the exit server, they cannot determine your true IP address or match browsing activity to your identity.
When to Use Secure Core
Enable Secure Core when:
- Accessing sensitive information on public WiFi
- Conducting activities requiring maximum anonymity
- Connecting from countries with aggressive surveillance
- Protecting against targeted attacks
To activate: Select a Secure Core server from the Countries tab in your application. Note that using Secure Core reduces connection speeds by approximately 30-40% due to the additional routing.
Optimizing Performance Without Compromising Security
VPN Accelerator Technology
Proton VPN’s unique VPN Accelerator can increase speeds by up to 400% without compromising security. This technology suite includes:
- Performance-based server selection algorithms
- Advanced networking techniques to reduce latency
- TCP congestion control optimization
- Enhanced routing protocols
VPN Accelerator works automatically with all protocols and requires no configuration. However, ensure it’s enabled in Settings → Features → VPN Accelerator.
Split Tunneling Configuration
Split tunneling allows you to exclude specific applications or IP addresses from the VPN tunnel. While this can improve performance for local services, use it judiciously as excluded traffic won’t be protected.
Configure split tunneling by:
- Opening Settings → Advanced → Split Tunneling
- Choosing between excluding specific apps or IP addresses
- Adding only absolutely necessary exclusions (like local network printers)
Never exclude browsers, email clients, or any application handling sensitive data from VPN protection.
Port Forwarding for P2P Activities
If you engage in peer-to-peer file sharing or online gaming, configure port forwarding for optimal performance. This feature, now available on Windows, macOS, and Linux, routes connections efficiently through the Proton VPN firewall.
Enable port forwarding only when connected to P2P-designated servers, and remember to disable it when not needed to minimize potential attack surface.
Platform-Specific Security Optimizations
Windows Configuration
Windows users should enable LAN blocking to prevent local network attacks—a critical feature added in version 4.2.0. Navigate to Settings → Advanced → LAN Connections and disable local network access while connected to the VPN.
Additionally, configure Windows Firewall rules to complement VPN protection using PowerShell administrative commands for enhanced security layers.
macOS Security Enhancements
Mac users should take advantage of the recently added port forwarding capabilities for improved P2P performance. When configuring system extensions for protocol changes, always verify authenticity using Touch ID or system password to prevent unauthorized modifications.
Mobile Device Protection
On Android and iOS devices, enable the Always-On VPN feature in your device settings to ensure continuous protection. Recent battery optimizations mean you can maintain VPN connections throughout the day with minimal impact on battery life—especially when using the efficient WireGuard protocol.
Creating Custom Connection Profiles
Developing Situation-Specific Profiles
Proton VPN’s connection profiles let you save customized settings for different scenarios. Create dedicated profiles for:
Maximum Security Profile:
- Protocol: OpenVPN TCP
- Server: Secure Core
- NetShield: Advanced
- Kill Switch: Advanced
Streaming Profile:
- Protocol: WireGuard
- Server: Optimized streaming servers
- NetShield: Standard (to avoid breaking video players)
- Kill Switch: Standard
Gaming Profile:
- Protocol: WireGuard UDP
- Server: Lowest latency P2P server
- Port Forwarding: Enabled
- Split Tunneling: Configure for game-specific optimization
Access profiles through the Profiles tab and switch instantly based on your current needs.
Monitoring and Maintaining Security
Regular Security Audits
Perform monthly security checks to ensure optimal protection:
- Verify your connection using ipleak.net to check for DNS, WebRTC, and IPv6 leaks
- Update to the latest app version for security patches and new features
- Review your account security settings and rotate passwords if necessary
- Check Proton VPN’s transparency reports for security updates
Understanding Connection Logs
While Proton VPN maintains a strict no-logs policy for user activity, the application provides local connection logs for troubleshooting. Review these periodically to identify unusual connection patterns or potential issues, but remember these logs remain entirely on your device.
Bypassing Censorship and Network Restrictions
Alternative Routing Technology
When facing aggressive censorship, Proton VPN’s alternative routing technology bypasses blocks by rerouting connections through third-party networks like AWS. This feature activates automatically when direct connections fail, ensuring continuous access even in restrictive environments.
Tor Over VPN Integration
For maximum anonymity, combine Proton VPN with the Tor network. Select Tor over VPN servers to route your traffic through both systems, accessing .onion sites directly from your regular browser while maintaining VPN protection as your first layer of defense.
Best Practices for Different Use Cases
For Remote Work and Business
When handling corporate data, always use:
- Secure Core servers for sensitive communications
- Advanced Kill Switch to prevent accidental exposure
- Dedicated business profiles with maximum security settings
- Regular security audits of connection logs
For Streaming and Entertainment
Optimize your streaming experience while maintaining privacy:
- Use Plus or Unlimited plans for access to streaming-optimized servers
- Connect to servers in your target content region
- Enable Smart Protocol for automatic optimization
- Keep NetShield on Standard to avoid breaking video players
For Privacy Activists and Journalists
Those facing elevated threats should:
- Always use Secure Core servers
- Enable Stealth protocol in restrictive regions
- Combine with Proton Mail for encrypted communications
- Use dedicated devices with VPN-only internet access
- Regularly verify no DNS or WebRTC leaks
Troubleshooting Common Security Issues
Connection Stability Problems
If experiencing frequent disconnections:
- Switch from UDP to TCP protocol
- Try different server locations
- Disable VPN Accelerator temporarily
- Check for ISP throttling using alternative routing
Performance Optimization
For improved speeds without compromising security:
- Connect to geographically closer servers
- Use WireGuard protocol when possible
- Ensure VPN Accelerator is enabled
- Avoid peak hours on popular servers
Future-Proofing Your Privacy Setup
As Proton VPN continues evolving with features like command-line interface for Linux and gaming optimizations planned for late 2025, staying informed ensures maximum protection. Subscribe to Proton’s blog for updates on new security features and emerging threats.
The service’s commitment to open-source development and regular independent audits means security improvements arrive frequently. Enable automatic updates in your app settings to receive critical security patches immediately upon release.
Conclusion: Building a Comprehensive Privacy Strategy
Maximizing data protection with Proton VPN requires more than just installing the application—it demands thoughtful configuration tailored to your specific threat model and use cases. By implementing these advanced settings and best practices, you create multiple layers of defense against surveillance, censorship, and cyber threats.
Remember that VPN protection is just one component of comprehensive online security. Combine Proton VPN with encrypted messaging, secure browsers, and good operational security practices for complete digital privacy. The investment in properly configuring your VPN today pays dividends in long-term privacy protection and peace of mind.
Whether you’re protecting sensitive business communications, bypassing censorship, or simply reclaiming your digital privacy, Proton VPN’s robust feature set—when properly configured—provides enterprise-grade security accessible to everyone. Start with the essential settings outlined here, then progressively implement advanced features as your comfort and needs evolve.



Comments (0)