
Notepad++ sat compromised for six months. Nobody noticed.
Between June and December 2025, hackers hijacked the popular text editor’s update system. They didn’t touch the program itself. Instead, they weaponized WinGUp, the mechanism that delivers updates to users. So every time someone clicked “update,” they potentially downloaded malware alongside legitimate software.
Don Ho, who’s maintained Notepad++ since 2003, finally confirmed the breach. His message was blunt: download version 8.9.1 manually. Don’t trust the automatic updater just yet.
The Update System Became the Weapon
WinGUp handles updates for Notepad++ and several other Windows applications. It’s supposed to fetch new versions from trusted servers. But hackers found a way to inject compromised executables into that pipeline.
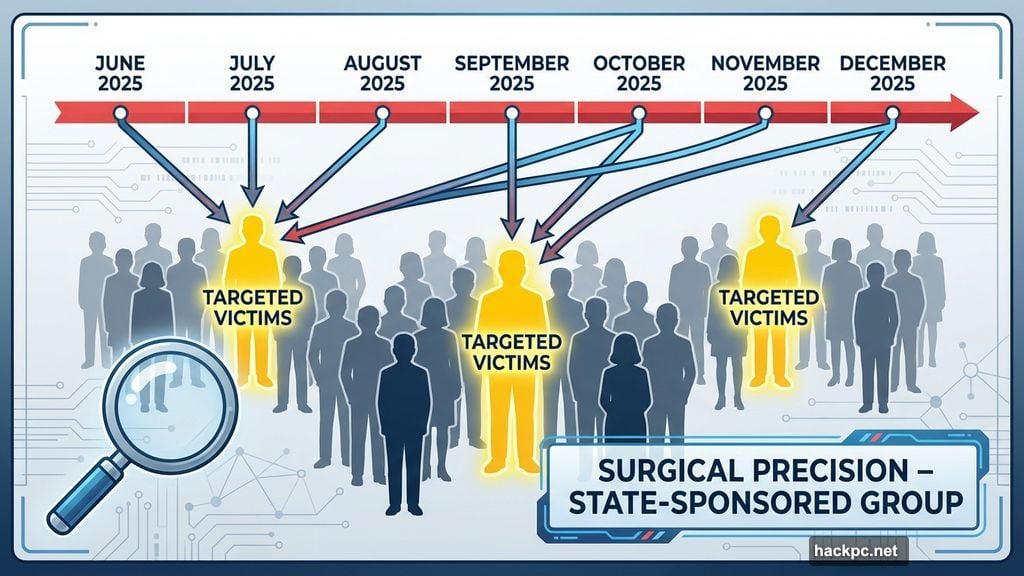
Here’s what made this attack clever. The malware didn’t spread to everyone. Instead, attackers selected specific targets carefully. Security researchers believe a Chinese state-sponsored group ran the operation, picking victims with surgical precision.
Most users never saw anything suspicious. Their updates completed normally. But a small subset received additional “gifts” with their software patches. Those extras likely included spyware designed to monitor activity or steal data.
The selective targeting kept the breach hidden for months. No mass infections. No obvious red flags. Just quiet surveillance of chosen individuals.
Notepad++ Itself Stayed Clean
Good news: the actual Notepad++ program never got corrupted. If you downloaded it directly from the official site, you received legitimate software.
The problem lived exclusively in the update delivery mechanism. So existing installations remained safe unless they pulled updates during that six-month window. Even then, only targeted users received malicious payloads.
This matters because millions of developers, writers, and power users rely on Notepad++. It’s been a Windows staple since 2003, offering features that Microsoft’s basic Notepad can’t match. Syntax highlighting, macro recording, plugin support – all the tools that make it essential for technical work.
But that popularity also makes it a juicy target. Compromise a tool used by developers and system administrators, and suddenly you have access to sensitive systems. That’s exactly why state-sponsored groups invest time in attacks like this.
Security Upgrades Are Live Now
Don Ho didn’t just acknowledge the problem. He rebuilt the infrastructure.
The official Notepad++ website now runs with stronger security protocols. The update provider got similar reinforcements. Plus, version 8.9.1 includes specific security enhancements designed to prevent future hijacking attempts.
Ho recommends skipping the automatic updater for now. Instead, visit the official site and download the latest version manually. That ensures you get clean software directly from the source, no compromised middleman involved.
Will these changes stop determined attackers? Ho seems cautiously optimistic. “With these changes and reinforcements, I believe the situation has been fully resolved. Fingers crossed,” he wrote. That “fingers crossed” tells you everything about software security – even with upgrades, absolute certainty doesn’t exist.
The Bigger Supply Chain Problem
This attack fits a disturbing pattern. Hackers increasingly target update mechanisms instead of applications themselves. Why break into a fortress when you can poison the supply line?
Think about it. Users trust updates. They’re trained to install them promptly. Security experts constantly nag about keeping software current. So when an update notification appears, most people click through without hesitation.

That trust becomes a vulnerability. Compromise the update channel, and you deliver malware to users who think they’re improving security. It’s psychological judo – using good security practices against people.
We’ve seen this before. The SolarWinds attack worked similarly, injecting malicious code into software updates for government agencies and major corporations. Attackers spent months preparing, then deployed their payload through trusted update channels.
Notepad++’s breach was smaller scale but used the same playbook. Find the update mechanism. Compromise it quietly. Select high-value targets. Deliver payloads disguised as legitimate updates. Operate undetected for as long as possible.
What You Should Do Right Now
First, check your Notepad++ version. Open the program, click “Help,” then “About Notepad++.” If you’re running anything older than 8.9.1, update immediately.
But don’t use the built-in updater. Visit the official Notepad++ website directly. Download version 8.9.1 from there. Install it manually. Yes, it’s extra steps. But those steps guarantee you’re getting clean software.
Second, consider your other software. Notepad++ isn’t unique in having an update mechanism. Almost every application you use has one. So apply the same skepticism elsewhere.
Check for updates from official sources when possible. Be suspicious of unexpected update prompts, especially from applications you rarely use. If something feels off, verify through the developer’s website before installing anything.
Third, remember that targeted attacks often fly under the radar. You might never see obvious symptoms. No performance degradation. No suspicious network traffic. Just quiet data collection running in the background.
The Trust Deficit Grows
This breach highlights a fundamental problem in modern computing. We rely on trust – in developers, in update systems, in digital signatures. But that trust creates single points of failure.
When attackers compromise a trusted system, they inherit all the access that trust provides. Users who diligently install updates become the most vulnerable. The security-conscious become the easiest targets.
Don Ho seems to understand this. His recommendation to manually download rather than auto-update shows awareness that trust needs rebuilding. The infrastructure got fixed, but user confidence takes longer to restore.
Notepad++ will survive this. It’s too useful and too established to fade away over one breach. But the incident reminds us that nothing – not even beloved open-source tools maintained by dedicated developers – exists beyond the reach of determined attackers.
Update your software. But verify first. Trust the people behind your tools. But not blindly. And always remember: the convenience of automatic updates comes with risks that aren’t always visible until months after the damage happens.


Comments (0)