As enterprise collaboration platforms become the nerve center of modern workplace communication, understanding their security implications has never been more critical. Slack, with its 38 million daily active users and adoption by 77% of Fortune 100 companies, presents both tremendous productivity benefits and significant security challenges that technical teams must navigate carefully. This comprehensive analysis explores the vulnerabilities, compliance requirements, and security best practices that engineering teams, security professionals, and IT administrators need to understand when deploying Slack in their organizations.
The Current State of Slack Security: A Complex Reality
Recent high-profile security incidents have thrust Slack into the spotlight, not necessarily due to fundamental platform vulnerabilities, but rather because of its central role in corporate communications. The 2024 Disney breach, where hacktivist group NullBulge leaked 1.1 terabytes of internal Slack communications, serves as a stark reminder that even the most sophisticated organizations remain vulnerable to determined threat actors exploiting human factors rather than technical weaknesses.
What makes these incidents particularly concerning for technical teams is their diversity. From prompt injection vulnerabilities in Slack AI discovered by PromptArmor to social engineering attacks that compromised Uber’s workspace security in 2022, the attack surface extends far beyond traditional software vulnerabilities. These breaches demonstrate that securing workplace collaboration tools requires a holistic approach combining technical controls, security policies, and continuous monitoring of both internal and external threats.
Understanding Core Security Architecture and Compliance Standards
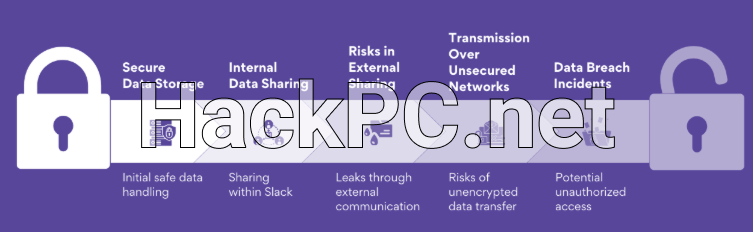
Slack’s security infrastructure operates on multiple layers, implementing industry-standard encryption protocols for data both at rest and in transit. The platform maintains compliance with major security frameworks including SOC 2, SOC 3, and ISO 27001, providing technical teams with assurance about baseline security controls. However, understanding the shared responsibility model becomes crucial – while Slack secures the platform infrastructure, organizations must properly configure security settings, manage user access controls, and implement appropriate data governance policies.
The platform’s Enterprise Key Management (EKM) capability offers organizations additional control over encryption keys, enabling compliance with stringent regulatory requirements in healthcare, finance, and government sectors. For technical teams operating under HIPAA, FINRA, or FedRAMP requirements, Slack provides configuration options that support compliance, though proper implementation requires careful planning and ongoing monitoring of security configurations to prevent misconfiguration vulnerabilities that could expose sensitive data.
Critical Vulnerabilities and Attack Vectors Technical Teams Must Address
Authentication and Access Control Weaknesses
The authentication layer represents one of the most critical security boundaries in any collaboration platform. While Slack supports single sign-on (SSO) integration with major identity providers and multi-factor authentication, configuration errors can create significant vulnerabilities. Security researcher Frans Rosén’s discovery of an authentication bypass vulnerability, though quickly patched by Slack, highlighted how subtle flaws in authentication workflows can enable complete account takeover, granting attackers access to entire conversation histories, shared files, and integrated third-party services.
Technical teams must implement robust identity and access management strategies, including regular audit of user permissions, enforcement of strong authentication policies, and continuous monitoring of authentication logs for anomalous patterns. The complexity increases exponentially when managing external collaborators through Slack Connect, where security boundaries extend beyond organizational control, requiring additional verification mechanisms and careful consideration of data sharing policies across organizational boundaries.
API Security and Third-Party Integration Risks
Slack’s extensive ecosystem of third-party integrations, while enhancing productivity, significantly expands the attack surface. Each integrated application represents a potential entry point for malicious actors, particularly when these integrations have broad permissions to read messages, access files, or post content across multiple channels. The platform’s API security becomes critical when custom integrations or workflow automations handle sensitive data, requiring thorough security reviews, regular permission audits, and implementation of least-privilege access principles.
Security incidents involving third-party applications have demonstrated how compromised integrations can exfiltrate data without triggering traditional security monitoring systems. Technical teams need to establish governance frameworks for application approval, implement continuous monitoring of API usage patterns, and maintain inventories of all active integrations with their associated permission scopes. Regular security assessments of critical integrations should become standard practice, particularly for applications with access to sensitive channels or data.
Insider Threats and Data Loss Prevention Challenges
The insider threat vector presents unique challenges in collaborative environments where information sharing is essential for productivity. Slack’s design philosophy emphasizes openness and accessibility, which can conflict with security requirements for data compartmentalization. The platform’s search capabilities, while powerful for legitimate users, can be exploited by malicious insiders to discover and exfiltrate sensitive information from channels they shouldn’t access or from historical conversations predating current security policies.
Implementing effective data loss prevention strategies requires combining Slack’s native DLP capabilities with third-party security tools that provide deeper content inspection and behavioral analytics. DoControl’s analysis of recent breaches emphasizes the importance of anomaly detection systems that can identify unusual data access patterns, bulk file downloads, or suspicious message forwarding that might indicate insider threat activity. Technical teams should implement comprehensive audit logging, regular access reviews, and automated alerting for high-risk activities.
Emerging Threats: AI Integration and Prompt Injection Vulnerabilities
The introduction of Slack AI has created new attack vectors that security professionals are only beginning to understand fully. The prompt injection vulnerability discovered in August 2024 demonstrated how attackers could potentially extract data from private channels through carefully crafted prompts, exploiting the AI’s ability to search across workspace content. This represents a paradigm shift in security thinking – traditional access controls become insufficient when AI systems can aggregate and synthesize information across security boundaries.
Technical teams deploying Slack AI must understand that these features introduce novel risks requiring new security approaches. Prompt injection attacks can bypass traditional security controls by manipulating the AI’s context window, potentially exposing API keys, authentication tokens, or other sensitive data stored in seemingly secure channels. Organizations should implement strict policies governing AI feature usage, establish monitoring for suspicious AI interactions, and consider whether the productivity benefits outweigh the expanded attack surface.
Building Comprehensive Security Strategies for Enterprise Slack Deployments
Security Configuration Best Practices
Proper configuration of Slack’s security features forms the foundation of any defensive strategy. Technical teams should enable Enterprise Mobility Management (EMM) to control device access, implement IP whitelisting for administrative functions, and configure session timeout policies appropriate to their risk tolerance. Channel creation policies should restrict who can create public channels, while guest access requires careful governance to prevent unauthorized data exposure.
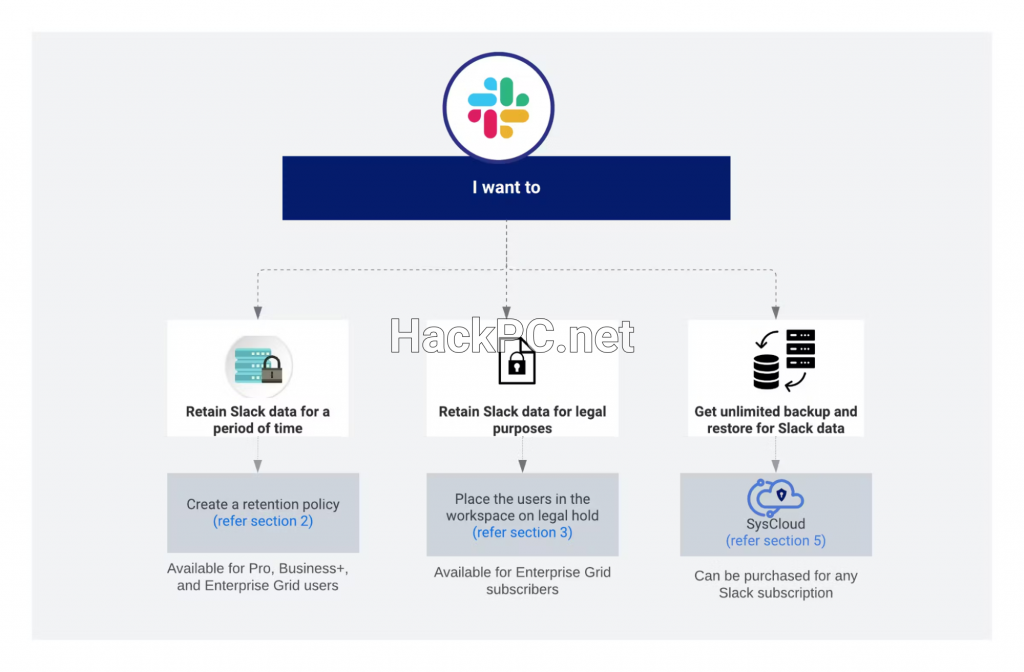
Data retention policies deserve particular attention, balancing compliance requirements with security considerations. While longer retention periods may satisfy regulatory requirements, they also increase the potential impact of any breach. Organizations should implement granular retention policies that differentiate between channel types and data sensitivity levels, automatically purging unnecessary historical data while preserving records required for compliance or legal holds.
Monitoring and Incident Response Capabilities
Effective security monitoring requires integrating Slack’s audit logs with Security Information and Event Management (SIEM) platforms to enable real-time threat detection. Technical teams should establish baselines for normal user behavior, enabling detection of anomalies such as unusual login locations, bulk message deletions, or excessive file downloads. Mimecast’s compliance monitoring guidance emphasizes the importance of automated alerting for policy violations and suspicious activities.
Incident response plans must specifically address Slack-related scenarios, including account compromise, data exfiltration, and malicious bot activity. Regular tabletop exercises should test response procedures, ensuring teams can quickly isolate compromised accounts, preserve evidence for forensic analysis, and communicate effectively during security incidents. Integration with broader security orchestration platforms enables automated response actions, reducing the window of opportunity for attackers.
Compliance and Regulatory Considerations
Organizations operating under regulatory frameworks like GDPR, CCPA, or industry-specific requirements must carefully configure Slack to maintain compliance. Data residency controls allow organizations to specify geographic regions for data storage, addressing sovereignty concerns and regulatory requirements. However, technical teams must understand that compliance extends beyond configuration – it requires ongoing monitoring, regular audits, and documentation of security controls.
The eDiscovery capabilities become critical during legal proceedings or regulatory investigations. Technical teams should establish procedures for legal holds, ensure proper chain of custody for exported data, and maintain audit trails demonstrating compliance with data handling requirements. Global Relay’s compliance guidance highlights the importance of integrating Slack with enterprise-grade archiving solutions that provide tamper-proof records and sophisticated search capabilities required for regulatory compliance.
Future-Proofing Slack Security: Emerging Technologies and Evolving Threats
As workplace collaboration continues evolving, security strategies must adapt to emerging threats and technologies. The integration of artificial intelligence, while enhancing productivity, introduces new attack surfaces requiring novel defensive approaches. Zero-trust architectures, behavioral analytics, and machine learning-based threat detection represent the future of collaboration platform security, moving beyond perimeter-based defenses to continuous verification and risk assessment.
Technical teams should prepare for increased sophistication in social engineering attacks targeting collaboration platforms. Deepfake technology, AI-generated phishing messages, and coordinated disinformation campaigns will challenge traditional security awareness training. Organizations must invest in advanced threat intelligence capabilities, participate in information sharing communities, and maintain vigilance against evolving attack methodologies that exploit human psychology rather than technical vulnerabilities.
Critical Recommendations for Technical Teams
Successfully securing Slack deployments requires balancing security requirements with usability needs while maintaining regulatory compliance. Technical teams should prioritize implementing comprehensive security configurations, establishing robust monitoring capabilities, and maintaining ongoing security awareness programs. Regular security assessments, including penetration testing and configuration reviews, help identify vulnerabilities before malicious actors exploit them.
The shared responsibility model means that while Slack provides a secure platform foundation, ultimate security depends on proper implementation, configuration, and ongoing management by customer organizations. Technical teams must view Slack security as an ongoing process rather than a one-time configuration, continuously adapting to new threats, platform updates, and evolving business requirements. By understanding both the platform’s capabilities and limitations, organizations can leverage Slack’s collaborative benefits while maintaining appropriate security postures.
Organizations should report suspected vulnerabilities through Slack’s bug bounty program, contributing to the platform’s overall security improvement while potentially identifying issues before they impact production environments. This collaborative approach to security, combining vendor capabilities with customer vigilance, represents the most effective strategy for securing modern collaboration platforms in an increasingly complex threat landscape.
Conclusion: Navigating the Security-Productivity Balance
Slack security concerns reflect broader challenges facing organizations adopting cloud-based collaboration platforms. While the platform offers robust security features and compliance certifications, recent incidents demonstrate that technical controls alone cannot guarantee security. Success requires combining technical safeguards with organizational policies, user education, and continuous monitoring to create defense-in-depth strategies that protect sensitive data without hampering productivity.
Technical teams must approach Slack security with nuanced understanding, recognizing that perfect security remains unattainable while striving for continuous improvement. By implementing comprehensive security strategies, maintaining vigilance against emerging threats, and fostering security-conscious cultures, organizations can realize collaboration benefits while managing associated risks. The key lies not in avoiding collaboration platforms but in implementing them thoughtfully, with full awareness of security implications and appropriate controls to mitigate identified risks.



Comments (0)