
Substack exposed user data for four months. The platform only caught it this week.
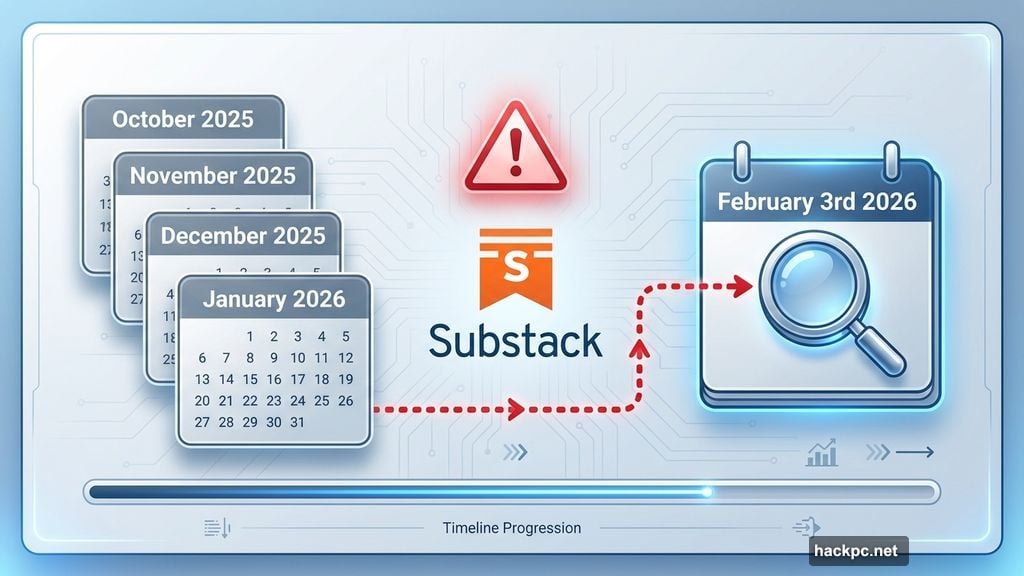
On February 3rd, Substack discovered a breach that started back in October. Hackers accessed email addresses, phone numbers, and internal metadata without authorization. So thousands of users just learned their contact information sat exposed for months.
The timing raises questions. Why did it take Substack four months to detect unauthorized access to user data? Plus, the company isn’t saying how many people got affected or what exactly went wrong.
The Breach Timeline Doesn’t Add Up
October 2025: Hackers gain unauthorized access to Substack’s internal systems. Nobody notices.
November through January: The breach continues undetected for three full months.
February 3rd, 2026: Substack finally identifies “evidence of a problem” with their security.
That’s a long time for a breach to go unnoticed. Modern security systems usually flag unauthorized access within hours or days. So either Substack’s monitoring tools failed, or the attackers were sophisticated enough to hide their tracks.
CEO Chris Best sent emails to affected users explaining the situation. But here’s what’s missing: specific details about what went wrong, how many users got hit, or why detection took so long.
What Data Got Exposed
The good news? Your passwords and credit card numbers stayed secure. Substack says financial information wasn’t compromised.
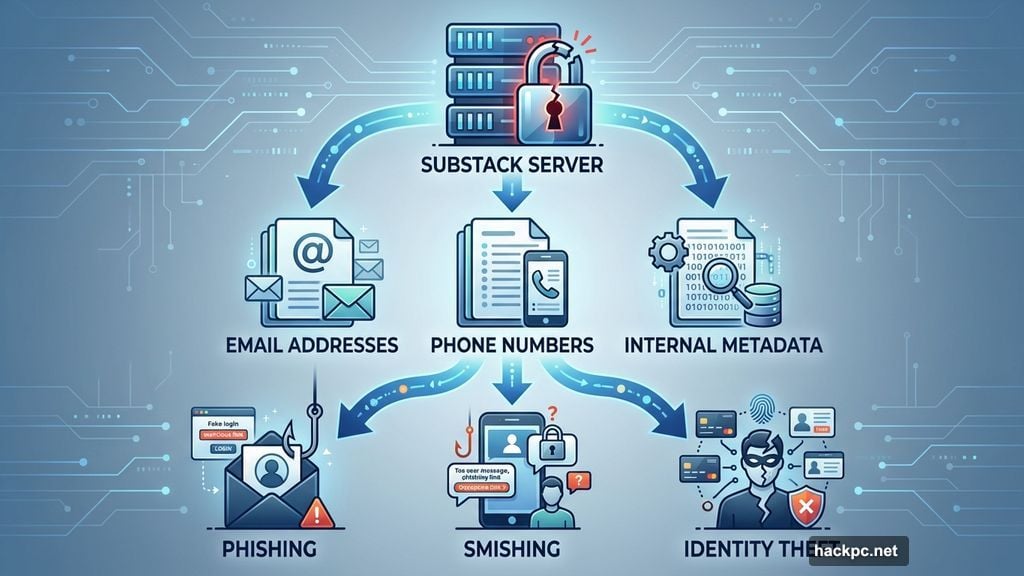
The bad news? Attackers accessed email addresses, phone numbers, and “internal metadata.” That last part is vague. Metadata could include anything from account creation dates to subscription patterns to reading habits.
Email addresses alone create risk. Attackers can use them for targeted phishing campaigns. They know you use Substack, so fake emails pretending to be from the platform will look more credible.
Phone numbers add another vector. Text message phishing (smishing) is growing fast. People trust texts more than emails, making them easier targets.
Moreover, combining emails with phone numbers lets attackers cross-reference data from other breaches. That helps build detailed profiles for identity theft or targeted scams.
The Response Feels Incomplete
Substack fixed the security problem. Great. They’re investigating and strengthening systems. Also good.
But the notification to users lacks critical information. How many people got affected? What specific vulnerability did hackers exploit? Are there signs the stolen data is circulating online?
Best’s apology sounds genuine. “I’m incredibly sorry this happened. We take our responsibility to protect your data and your privacy seriously, and we came up short here.”
Yet sorry doesn’t answer the practical questions. Users need concrete information to assess their risk and take appropriate action.
Interestingly, not all Substack users received the notification email. Some Verge staff members with accounts didn’t get warned. That suggests either the breach affected specific user segments, or Substack’s notification process itself has issues.
What This Means for Your Security
First, assume your Substack email is now public. Expect an uptick in phishing attempts. Be skeptical of any email claiming to be from Substack, especially if it asks you to click links or provide information.
Second, watch for suspicious text messages. If you provided a phone number to Substack, attackers have it. Don’t trust texts asking you to verify accounts or click urgent links.
Third, consider the metadata angle. If hackers grabbed subscription lists, they know what newsletters you read. That information helps craft convincing social engineering attacks. A fake email from a newsletter you actually subscribe to is harder to spot.
Fourth, monitor for credential stuffing attempts. If you reused your Substack password elsewhere, change it now. Attackers often try leaked credentials on multiple platforms.
The Bigger Platform Security Problem
This breach highlights a troubling pattern. Platforms detect breaches months after they happen. Users learn about exposure long after damage could have occurred.
Substack isn’t alone. Major platforms regularly announce breaches that started months or years earlier. Detection lag time creates a window where attackers operate freely before anyone notices.
Plus, breach notifications often lack specifics. Companies say “some users” were affected or “limited data” was exposed. That vagueness makes it impossible for users to gauge their actual risk.
The industry needs better standards. How quickly must companies detect unauthorized access? What specific information belongs in breach notifications? When should platforms notify regulators versus users?
Right now, companies self-regulate. That’s clearly not working well enough.
What You Should Do Now
Change your Substack password immediately. Yes, Substack says passwords weren’t exposed. But defense in depth matters. Use a unique, strong password you don’t use anywhere else.
Enable two-factor authentication if you haven’t already. That adds a layer of protection even if your password somehow gets compromised later.
Be extra vigilant about emails and texts for the next few months. Verify sender authenticity before clicking any links. When in doubt, navigate directly to websites instead of clicking links in messages.
Consider using email aliases for newsletter subscriptions. Services like SimpleLogin or Apple’s Hide My Email let you create unique addresses for each platform. If one gets compromised, you only need to replace that specific alias.
Finally, accept that your Substack email is probably already in attacker databases. There’s no evidence yet that the stolen data is being actively misused. But breached data tends to circulate. Plan accordingly.
Four months is too long to detect a breach. Companies need better security monitoring. Users deserve faster notifications with complete information. Until that changes, we’re all just hoping platforms catch problems before too much damage happens.



Comments (0)